In today’s world, keeping data safe is a big challenge. Many people share private information every day, and finding the right balance between protecting it and allowing the proper access can be tricky.
That’s where data tokenization comes in—a method that can potentially improve data security, privacy, and compliance by preventing unauthorized access and misuse.
But, it’s crucial to implement it carefully and precisely to get the most out of it and avoid potential issues. This strategic approach is promising for safeguarding sensitive information, ensuring privacy, and meeting compliance standards.
This article explores the concept of data tokenization, how it works on the blockchain, and the benefits and possible use cases of this approach.
How Does Data Tokenization Work?
Data tokenization is a process that transforms sensitive information, such as credit card details or health data, into tokens. These tokens can be easily moved, stored, and processed without exposing the actual sensitive data.
Typically, these tokens are unique, unchangeable, and their authenticity can be verified on the blockchain. This enhances data security, privacy, and compliance.
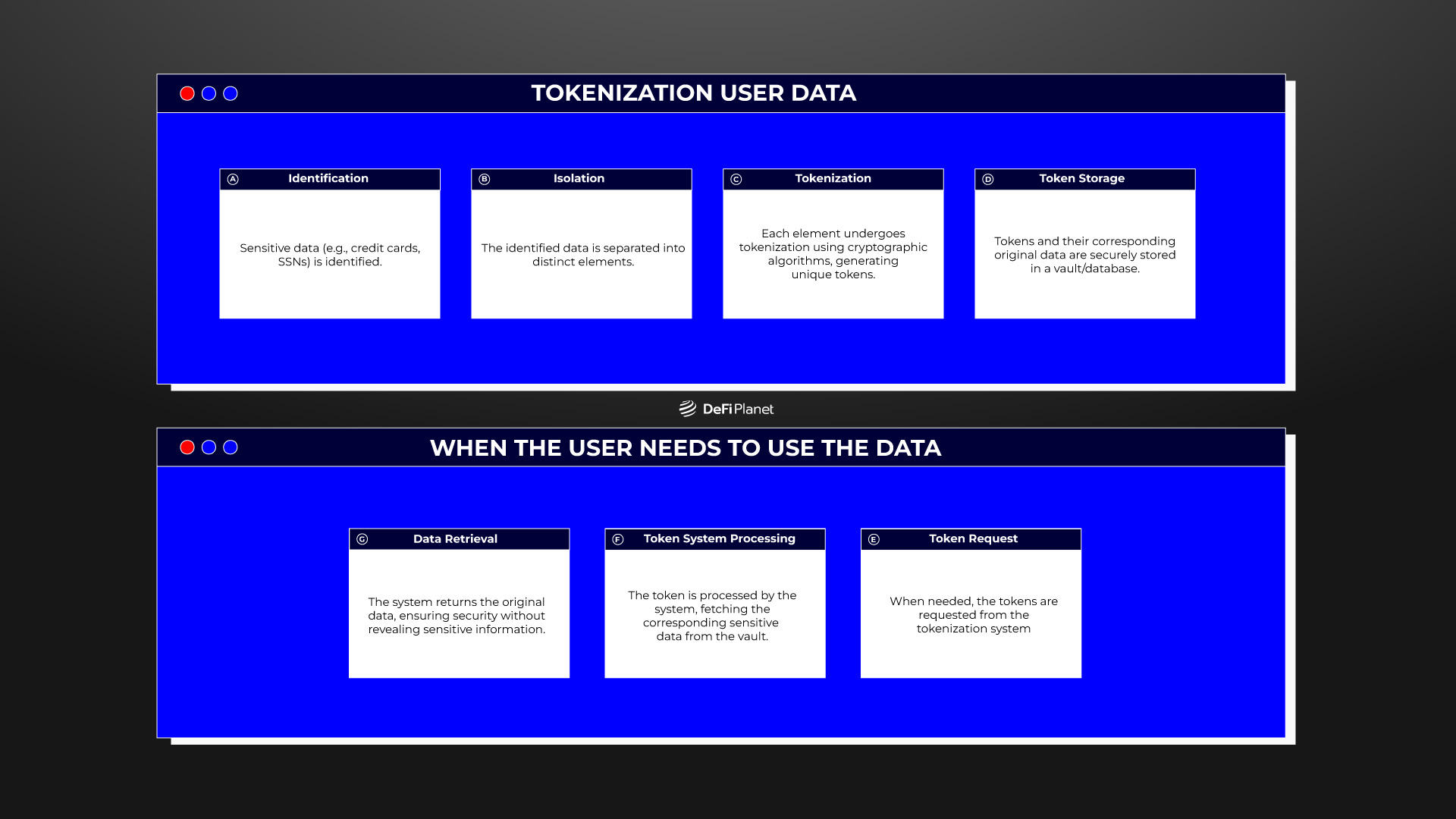
The process of data tokenization involves several key steps. First, sensitive data, like credit card or Social Security numbers, is identified and separated into individual components.
These components are then run through a tokenization system, generating unique tokens for each data element. These tokens, created using cryptographic algorithms to ensure uniqueness and randomness, replace the original sensitive data in the system, providing a secure layer.
The tokenization system includes a secure vault or database that stores the connection between the original sensitive data and its corresponding tokens.
When a token is required, such as in a transaction or data retrieval, it is sent to the tokenization system. This system retrieves the relevant sensitive data from the token vault and sends it back to the requesting system, facilitating seamless operations without exposing the actual sensitive information.
For instance, a credit card number can be tokenized into a random set of digits for payment verification without disclosing the actual card number. When the user needs it, the tokenization system sends the required data to the requesting system for quick verification.
Benefits of Data Tokenization
Data tokenization offers several advantages for individuals and organizations to enhance their data security and privacy. Here are some of the most significant benefits.
Improved Security
Data tokenization heightens security for any users by ensuring that whenever their data is used, it only exists as a token. The actual data is stored exclusively on a highly secure server with strict security protocols.
In the event of a data breach, unauthorized access to sensitive information, such as crypto addresses or wallet passwords, is thwarted, as attackers only gain access to useless tokens. For instance, compliance standards like PCI DSS or GLBA often mandate tokenization to fortify security.
During a data breach, scammers can’t easily access sensitive information like crypto addresses or wallet passwords. Instead, they only obtain a useless token, thanks to industry compliance standards like PCI DSS or GLBA, which often mandate tokenization providers to fortify security.
Streamlined Data Management
Handling sensitive data is often complex and risky. Tokenization simplifies this by allowing more straightforward data storage and transmission and reducing associated risks. Beyond enhancing data operation efficiency, it enables authorized systems and applications to work with tokens directly, avoiding the need for decryption or exposing sensitive information.
Scalability and Adaptability
Data tokenization caters to businesses of all sizes, from startups to large enterprises. Its scalability seamlessly adjusts to evolving business needs, and its flexibility allows compatibility with different data types, platforms, and applications. This makes it a robust solution, whether for small organizations or those experiencing dynamic requirements.
Increased Customer Trust
As data breaches can negatively impact a project’s reputation, showcasing data protection through tokenization fosters increased customer trust. When customers are aware of the commitment to data protection and security demonstrated by tokenization, they are more likely to trust the project with their information.
Compliance with Regulation
Some Industries face strict data protection rules, like HIPAA in healthcare or PCI DSS for card payment processing. Data tokenization is crucial for compliance and safeguarding sensitive data. Businesses would find blockchain services for data tokenization highly effective in meeting industry standards and fulfilling regulatory obligations.
Limitations of Data Tokenization
While data tokenization is an effective data security measure, it’s essential to be aware of its constraints and situations where it might not be the optimal solution. Here are key limitations to consider:
Handling Tokens Can Be Complex
Managing tokens, including encryption keys and mapping tables, can be intricate. Strong security practices are necessary to avoid token-related vulnerabilities. Secure tokenization relies on effective key management.
Organizations/Individuals must ensure that encryption keys used in the tokenization process are generated, stored, and rotated correctly. Inadequate key management procedures can risk the security of tokens and the sensitive data they represent.
Compatibility Challenges
Tokenized data may lose some usability on certain platforms because of incompatible formats. For instance, if you tokenize your email while signing up for one service, another platform designed for sending emails to users might face difficulty accurately delivering your mail.
The diverse systems and data handling methods across various blockchains, crypto exchanges, DApps, and DeFi ecosystems contribute to these interoperability and compatibility issues.
Tokenization System Risks
Despite enhancing data security, the tokenization system can be vulnerable if not well-protected. If cybercriminals breach the tokenization system, it could jeopardize the security of the entire set of tokenized data.
Implementing strong security measures like access controls, encryption, and monitoring is crucial to safeguard the tokenization system from potential threats. Regular security audits and updates are essential for effectively addressing these vulnerabilities.
Limited Protection Against All Threats
While tokenization is effective against various cyber threats, it doesn’t cover all types of attacks. For instance, it doesn’t prevent phishing attacks or social engineering attempts to access sensitive data.
Regulatory Compliance
While tokenization can help adhere to various data protection regulations, it’s vital to recognize it’s not a universal solution. Organizations and individuals must ensure their tokenization approach aligns with specific regulatory requirements to avoid penalties or non-compliance issues. Understanding the legal and regulatory aspects of tokenization is essential for maintaining data security and compliance.
Data Tokenization vs. Encryption
Data tokenization and encryption are both methods of data protection, but they vary in their approach and applications. Encryption transforms data into a coded format using algorithms, making it unreadable without the correct decryption key. On the other hand, tokenization replaces sensitive data with unique tokens that hold no inherent value.

The main difference lies in the security level offered. Encryption offers robust mathematical security, making it ideal for safeguarding data at rest or in transit.
Tokenization, on the other hand, emphasizes protecting data during processing and storage. Tokenization reduces the risk of exposing sensitive information by eliminating the need to decrypt data for authorized use, narrowing the potential attack surface.
Tokenization and encryption are not mutually exclusive; they can be combined for heightened security. Encrypting tokenized data adds an extra layer of protection. Even if tokens are compromised, the encrypted data remains secure.
Potential Use Cases of Data Tokenization
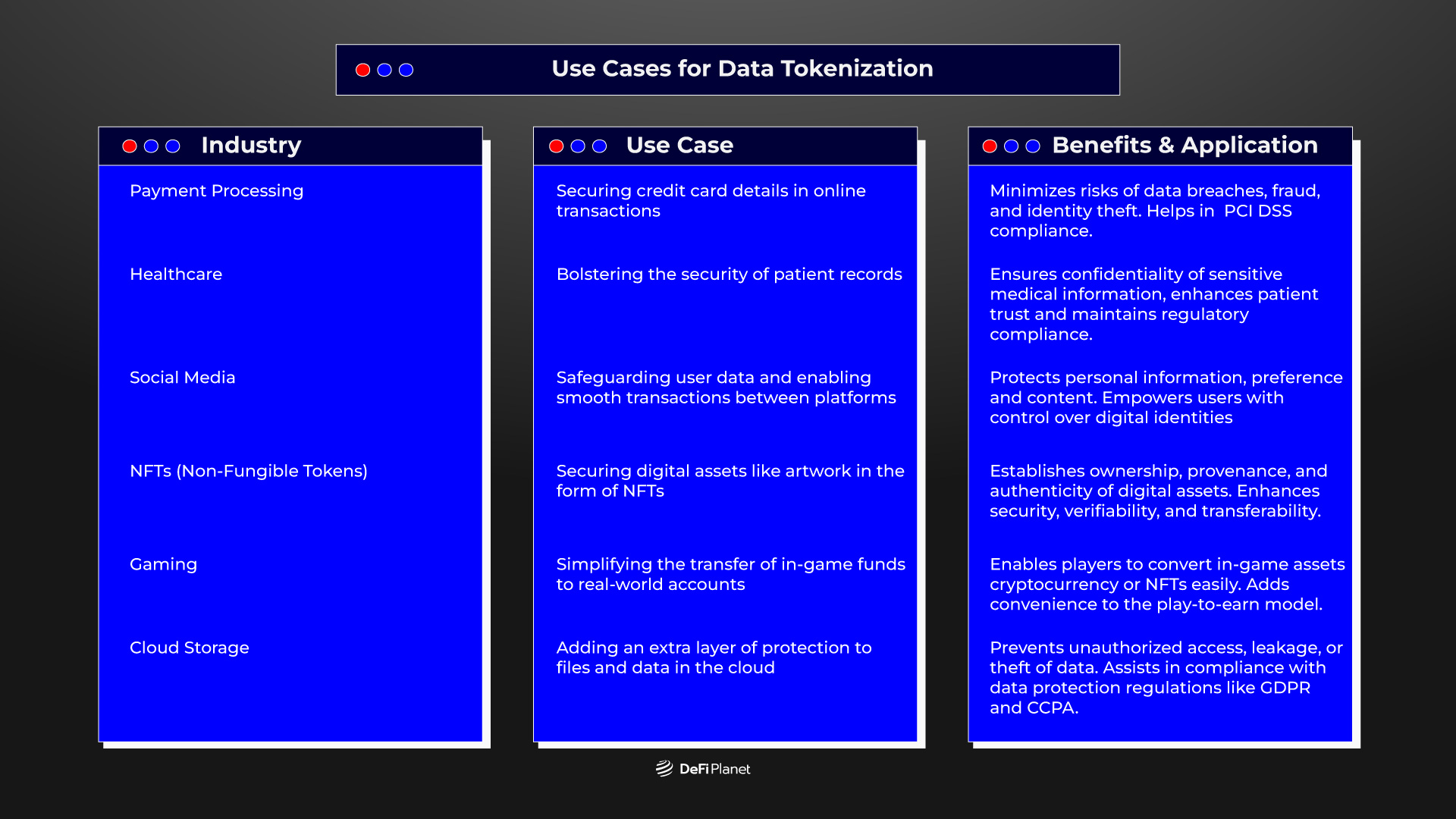
While data tokenization has been a staple in finance for securing payment details, its potential spans various industries. Beyond its traditional applications, data tokenization can be leveraged in some innovative ways across different sectors. Here are some noteworthy use cases:
These use cases highlight the versatility of data tokenization, extending beyond finance to various sectors such as healthcare, social media, digital art, gaming, and cloud storage, where it provides enhanced security and facilitates smoother data management.
In Conclusion, embracing data tokenization proves advantageous for those who prioritize user convenience and data security. Once users understand the concept and become acquainted with its functionality, employing data tokenization becomes an effortlessly straightforward and user-friendly process.
Disclaimer: This article is intended solely for informational purposes and should not be considered trading or investment advice. Nothing herein should be construed as financial, legal, or tax advice. Trading or investing in cryptocurrencies carries a considerable risk of financial loss. Always conduct due diligence.
If you would like to read more articles (news reports, market analyses) like this, visit DeFi Planet and follow us on Twitter, LinkedIn, Facebook, Instagram, and CoinMarketCap Community.
“Take control of your crypto portfolio with MARKETS PRO, DeFi Planet’s suite of analytics tools.”