Cryptocurrencies can be obtained in two ways: buying or mining. Binance and Coinbase are examples of cryptocurrency exchanges where you can buy cryptocurrencies. On the other hand, the process of cryptocurrency mining allows miners to earn cryptocurrency as a reward for solving a mathematical problem.
Because cryptocurrencies run on distributed ledgers known as blockchains, the digital database is constantly updated to include the most recent transaction information. Miners provide computing power to generate blocks and are compensated for their efforts.
However, because mining requires massive amounts of electricity and expensive equipment, hackers all over the world attempt to mine cryptocurrency for free using malicious scripts. This type of cybercrime has been dubbed “cryptojacking,” a combination of the words “cryptocurrency” and “hijacking.”
This article comprehensively examines cryptojacking, explaining how it works as well as how to detect and prevent this type of illegal crypto mining.
What is Cryptojacking?
Cryptojacking infiltrates a user’s mobile or desktop device as a form of malware and then uses its resources to mine digital currencies. A cryptocurrency is a form of digital currency that adopts the form of a token or a coin.
Bitcoin is the most popular cryptocurrency, and roughly 3,000 other varieties of cryptocurrencies exist. Some cryptocurrencies, such as those used with credit cards, have transitioned into the real world. However, the vast majority of cryptocurrencies are still only accessible online.
Blockchains are distributed databases used by cryptocurrencies. Transactions that have occurred since the last update are recorded in the blockchain and added to it at regular intervals. A “block” is created when a complex algorithm finds that a group of recently processed transactions all happen at the same time.
New blocks can only be generated for cryptocurrencies if users contribute computing power. Users are rewarded with cryptocurrency in return for contributing computing power. Cryptominers are individuals or organizations that offer computing power in exchange for cryptocurrency.
When mining the larger cryptocurrencies, groups of miners often collaborate, each operating their own specialized computer rig to perform the necessary mathematical calculations.
This process consumes a lot of electricity. Currently, the Bitcoin network consumes more than 73TWh of electricity per year.
How Common is Cryptojacking?
After a slow start, cryptojacking has recently gained traction, particularly in 2017 and 2018. According to a Malwarebytes Labs report published in February 2018, malicious crypto mining was the most commonly detected fraudulent mining method as of September 2017. In October 2017, Fortune predicted that cryptojacking would be a top security concern.
The number of Android devices infected with cryptojacking malware increased by 4,000% during the first quarter of 2018. During this period, cryptojackers upped their game and began targeting more advanced systems. For instance, criminals cryptojacked the control system of a European water utility and reduced the efficiency with which the utility’s employees could run the plant.
According to the same report, a team of Russian scientists mined Bitcoin using the supercomputer at their nuclear research and warhead facility.
While other types of malware (such as ransomware in 2021) have become popular and garnered international attention, cryptojacking has emerged as a consistent threat in recent years.
Cryptojacking may not be as newsworthy as it was in 2017 and 2018, but it remains a low-risk way for threat actors to profit from other people’s resources, so it is critical to take necessary precautions.
How Does Cryptojacking Work?
As stated earlier, mining is a legitimate means by which new coins can be created and added to the market in the cryptocurrency industry. To make this process work, miners compete to see who can solve a complex computational problem the fastest. Only when this issue is resolved will blocks of confirmed cryptocurrency transactions be added to the blockchain.
In essence, miners are being compensated for performing the function of auditors. They are in charge of Bitcoin transaction verification. Mining is important because it is the only way for a new cryptocurrency to enter circulation. It also helps miners earn money and keeps the Bitcoin ecosystem running.
Coin mining, the process by which people can earn cryptocurrency, is computationally and electrically intensive. Most cryptocurrency systems are structured so that the mining process gradually becomes more difficult, and its rewards are reduced.
An increase in mining difficulty implies that miners must expend more computing power to mine a block. This makes mining coins for legitimate cryptocurrencies a progressively expensive endeavour. It also indicates increased miner participation; as more nodes join, the mining process becomes more computationally demanding.
For example, to maintain the addition of new blocks to the Bitcoin blockchain, the Bitcoin network has an automatic system that adjusts the mining difficulty based on how many validators are participating in the mining process.
This system ensures that verifying and adding a new block of transactions takes approximately 10 minutes.
Without the system, validators could verify and add blocks very quickly and easily. This would result in more bitcoins entering circulation, and the hard cap of 21 million coins would be reached much sooner than the estimated year 2140.
Cybercriminals reduce mining expenses by stealing computing and energy resources. They use various hacking techniques to gain access to computers, then instruct those computers to perform illegal calculations and send the results to a server they control.
Cryptojackers employ the following strategies:
Download
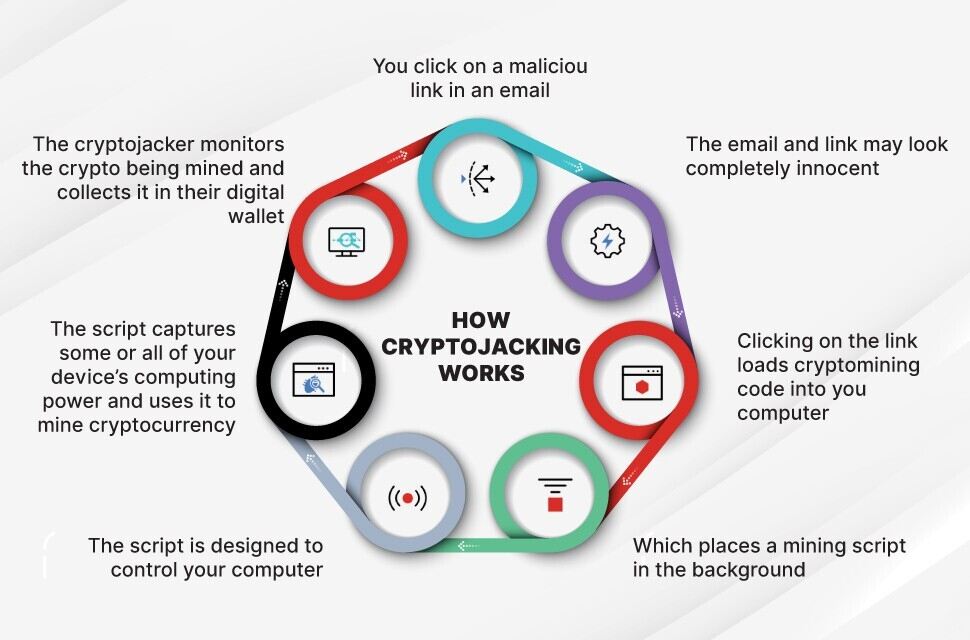
One tactic cryptojackers commonly use is to convince victims to download and run crypto-mining software. This is accomplished through social engineering techniques such as phishing, in which targets receive an email that appears genuine and baits them into clicking on a link. A malicious script is executed once the user clicks the link and the crypto-mining software is installed on the device. The script then runs in the background once the individual starts working.
Injection
Alternatively, a script could be embedded in an ad or website, which would then be published across numerous domains. The script is automatically executed once the victim visits the infected website or views the malicious advertisement in their browser. There is no malicious software on the victim’s computer. In both approaches, malicious code is executed on the victim’s machine, with the results sent to a server under the hacker’s control.
Hybrid
Attackers may combine both tactics to increase their chances of success. For example, 10% of the money made from cryptojacking could come from code installed on target machines, while the remaining 90% could come from users’ web browsers.
The diagram below sheds more light on how cryptojacking works:
How to Detect Cryptojacking
Identifying and blocking cryptojacking is essential because it prevents crypto from being mined on any computing platform without the users’ knowledge or consent. Detecting cryptojacking is difficult due to the numerous differences between it and traditional malware.
Cryptojackers don’t try to exert control over their victims as traditional malware does; instead, they exploit their resources. Malware can be used or added to websites that look legitimate because users are more likely to trust them and less likely to notice that their devices are being mined for data without their knowledge or consent.
Due to the high CPU usage associated with the cryptojacking process, the lifespan of the affected computers may be shortened, and they may even be damaged. The attacked user’s computer frequently overheats and performs abnormally poorly.
Computers that perform poorly, such as those with slow processing speeds or applications that crash regularly, may be the target of cryptojacking.
When a user stays on a website with cryptojacking scripts, the CPU is used more. Hence, if you suspect something nefarious is happening on your computer, you may want to check the CPU usage using the Task Manager.
How to Prevent Cryptojacking Attacks
It can be difficult to detect an intrusion after it has occurred, whether it occurred locally on a system or via a browser. Finding the source of excessive CPU usage can be just as challenging. Some processes may try to prevent the user from stopping the attack by disguising it as normal or hiding it in plain sight.
If the computer is operating at its maximum capacity, it will be extremely sluggish and difficult to troubleshoot, which is advantageous to cryptojackers. Installing security measures before malware infection is preferable to installing them afterward.
Users can disable JavaScript in their web browsers as a simple solution. The downside is that while this prevents drive-by cryptojacking, it may prevent the user from accessing some of their preferred or required features.
With the help of dedicated software such as “No Coin” and “MinerBlock,” popular web browsers can also be protected from being used for cryptocurrency mining.
In Conclusion,
- Cryptocurrency mining consumes enormous resources, but the rewards are usually substantial. Unfortunately, fraudulent actors have figured out how to use other people’s computers over the internet for crypto mining without their knowledge or consent.
- Cryptojacking involves infecting a device with malware to gain control of it, as opposed to the typical crypto hack, which involves stealing private keys belonging to a crypto wallet to empty it.
- Although detecting cryptojacking on a computer system can be difficult, taking the appropriate precautions to prevent cryptojacking and protect your computer and networking systems is critical.
If you would like to read more articles like this, visit DeFi Planet and follow us on Twitter, LinkedIn, Facebook, and Instagram.
“Take control of your crypto portfolio with MARKETS PRO, DeFi Planet’s suite of analytics tools.”





















